The dark web is a part of the internet that is intentionally hidden and is not accessible through standard web browsers or search engines like Google, Bing, or Yahoo. It is a subset of the deep web, which includes all parts of the internet that are not indexed by search engines. The dark web is characterized by its anonymity and lack of visibility to the general public.
Key characteristics of the dark web include:
- Anonymity: Users on the dark web often take steps to conceal their identity and location. This is typically achieved through specialized software like Tor (The Onion Router), which routes internet traffic through a series of servers, making it difficult to trace the source.
- Specialized URLs: Dark web websites typically have URLs with the “.onion” domain suffix, which can only be accessed using Tor or other similar tools.
- Encryption: Many websites and communications on the dark web use encryption to protect user privacy and security.
- Restricted Access: Access to the dark web is not open to everyone. Users often need specific knowledge, software, and configurations to access it.
The dark web is often associated with illegal activities due to its anonymity and lack of regulation. While it is true that some users engage in illegal activities on the dark web, such as the sale of drugs, firearms, stolen data, and hacking services, it’s essential to note that not everything on the dark web is illegal. It also serves as a platform for privacy-conscious individuals, journalists, and activists to communicate securely and access information without fear of censorship.
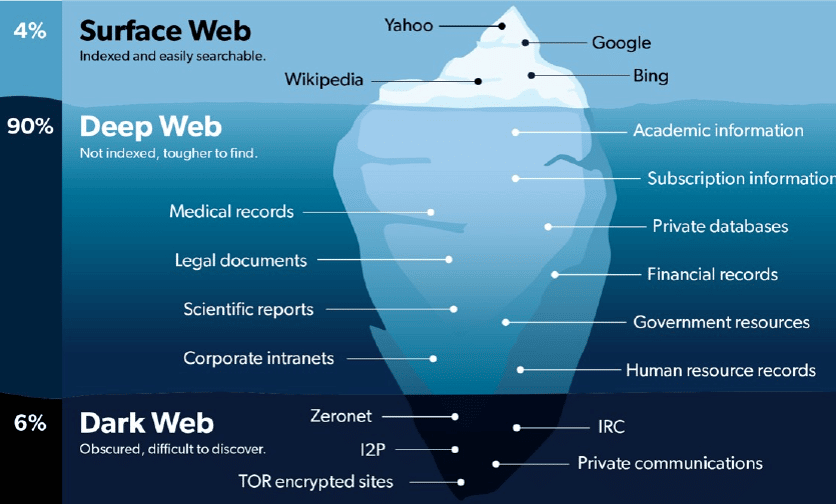
Criminals are drawn to the dark web for several reasons:
- Anonymity: The dark web provides a high degree of anonymity for its users. Criminals can conduct their activities without revealing their real identities or locations, making it challenging for law enforcement to track them down.
- Encrypted Communication: Dark web platforms often use encryption to secure communications and transactions. This encryption adds an extra layer of security, making it difficult for authorities to intercept and decipher messages.
- Access to Illicit Goods and Services: The dark web hosts marketplaces where various illegal goods and services are bought and sold. This includes drugs, firearms, stolen data, counterfeit currency, hacking tools, and more. Criminals can access a wide range of illegal commodities on these platforms.
- Censorship Resistance: Some criminals may use the dark web as a means to circumvent censorship and monitoring in their own countries. Journalists, activists, and dissidents in oppressive regimes might use the dark web to communicate and share information without fear of government intervention.
- Ease of Money Laundering: Cryptocurrencies like Bitcoin are commonly used for transactions on the dark web. Criminals can use these digital currencies to launder money and move funds across borders with relative ease.
- Community and Support: The dark web also provides a sense of community for like-minded individuals engaged in illegal activities. Criminals can connect with others who share their interests, exchange knowledge, and collaborate on criminal endeavors.
A wide range of sensitive personal data is available for sale on the dark web, and it can include:
- Financial Information:
- Stolen credit card information, including card numbers, expiration dates, and CVV codes.
- Bank account details, such as account numbers and login credentials.
- PayPal and other online payment account credentials.
- Personal Identification Information (PII):
- Social Security numbers (in the United States) or national identification numbers (in other countries).
- Driver’s license and passport information.
- Birth certificates and other government-issued documents.
- Healthcare Data:
- Medical records containing sensitive patient information.
- Health insurance details, including policy numbers.
- Login Credentials:
- Usernames and passwords for various online accounts, such as email, social media, and e-commerce websites.
- Corporate login credentials, which can be used for corporate espionage or unauthorized access to sensitive business information.
- Personal Communication:
- Private emails and chat logs, which may contain sensitive or confidential conversations.
- Personal photographs and videos.
- Hacked Data Dumps:
- Large datasets from data breaches, which can include a combination of personal information, such as names, addresses, email addresses, and more.
- Authentication Information:
- Biometric data, such as fingerprints or facial recognition data.
- Security question answers used for account recovery.
- Criminal Records and Background Checks:
- Information related to individuals’ criminal histories or background checks, which can be used for identity theft or blackmail.
- Education Records:
- Academic transcripts, diplomas, or certificates.
- Intellectual Property:
- Stolen intellectual property, such as proprietary software, copyrighted content, or trade secrets.
- Personal Profiles and Dossiers:
- Compiled profiles of individuals with a combination of personal and online activity data, which can be used for various malicious purposes.